Partner Platform Microsoft 365 DMI whitelisting
Read this article in: Deutsch
Prerequisites / Who can use DMI?
You can use Microsoft DMI if your organization meets these conditions:
Your mailboxes are hosted entirely on Microsoft 365 Exchange Online.
All users receiving the simulation emails are in a single Microsoft 365 tenant.
All email domains are owned and managed by your organization.
Limitations
DMI is not supported in the following cases:
You use an on-premise or hybrid Exchange server.
Users are spread across multiple Microsoft 365 tenants.
You use non-company domains (e.g.,
@hotmail.com).
DMI injects an email directly into a mailbox, bypassing standard delivery filters.
However, post-delivery security tools, such as Microsoft Defender, still process emails after they arrive. You must still configure any post-delivery tools - as explained in Partner Platform Microsoft 365 additional configurations - to ensure our simulation emails are not quarantined or flagged.
Defender is included in the following Microsoft plans:
Office 365 E5,
Microsoft 365 E5 Security
Microsoft 365 E5 include Microsoft Defender for Office P2 licenses
Microsoft 365 Business Premium includes Microsoft Defender for Office 365 P1 licenses.
See full details here.
Benefits of using DMI
Here are the main advantages of using DMI over standard SMTP delivery:
Improved email delivery: Traditional SMTP delivery can cause simulation emails to be caught by spam filters or quarantined. DMI bypasses these filters by delivering emails directly via a secure API connection, ensuring they reach user inboxes.
Simplified whitelisting & less maintenance: You no longer need to whitelist or maintain our list of IP addresses. With DMI, you only need to grant access to our Azure Enterprise App, giving you more effective control over system access.
Quicker setup: The setup process is faster as it reduces the dependency on your IT team for mail server changes. This allows you to launch your awareness program more quickly.
What permissions does SoSafe require in Microsoft Entra ID?
To create the SoSafe Email Connector, we require a Microsoft 365 account with Microsoft Entra ID administrator rights. However, after the creation, only two permissions are needed to deliver simulated phishing emails through DMI:
user.readbasic.all: Allows SoSafe to read basic user profiles within Microsoft Entra ID.
mail.readwrite: Enables SoSafe to identify inbox locations and inject phishing simulations correctly.
For further assistance, contact SoSafe Support or your Point of Contact.
Configure Microsoft DMI integration
Go to the client settings in SoSafe’s Partner Platform and open the Whitelisting menu item on the left side.
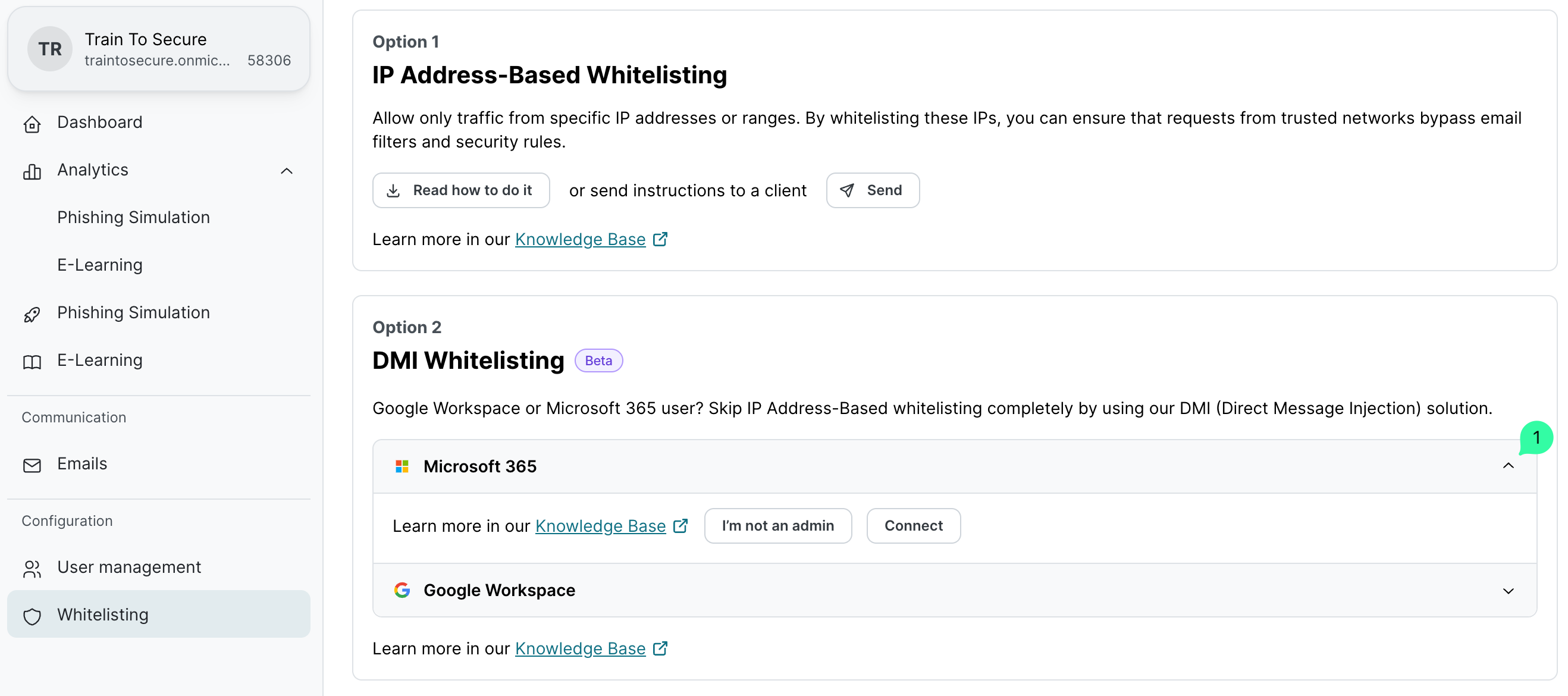
Under DMI Whitelisting, expand the Microsoft 365 option and select one of the following options:
If you have a Microsoft 365 account with Microsoft Entra ID administrator rights:
Click Connect to open the Microsoft Sign in page.
Log in with your Microsoft admin account.
Review the required permissions for the SoSafe Email Connector application.
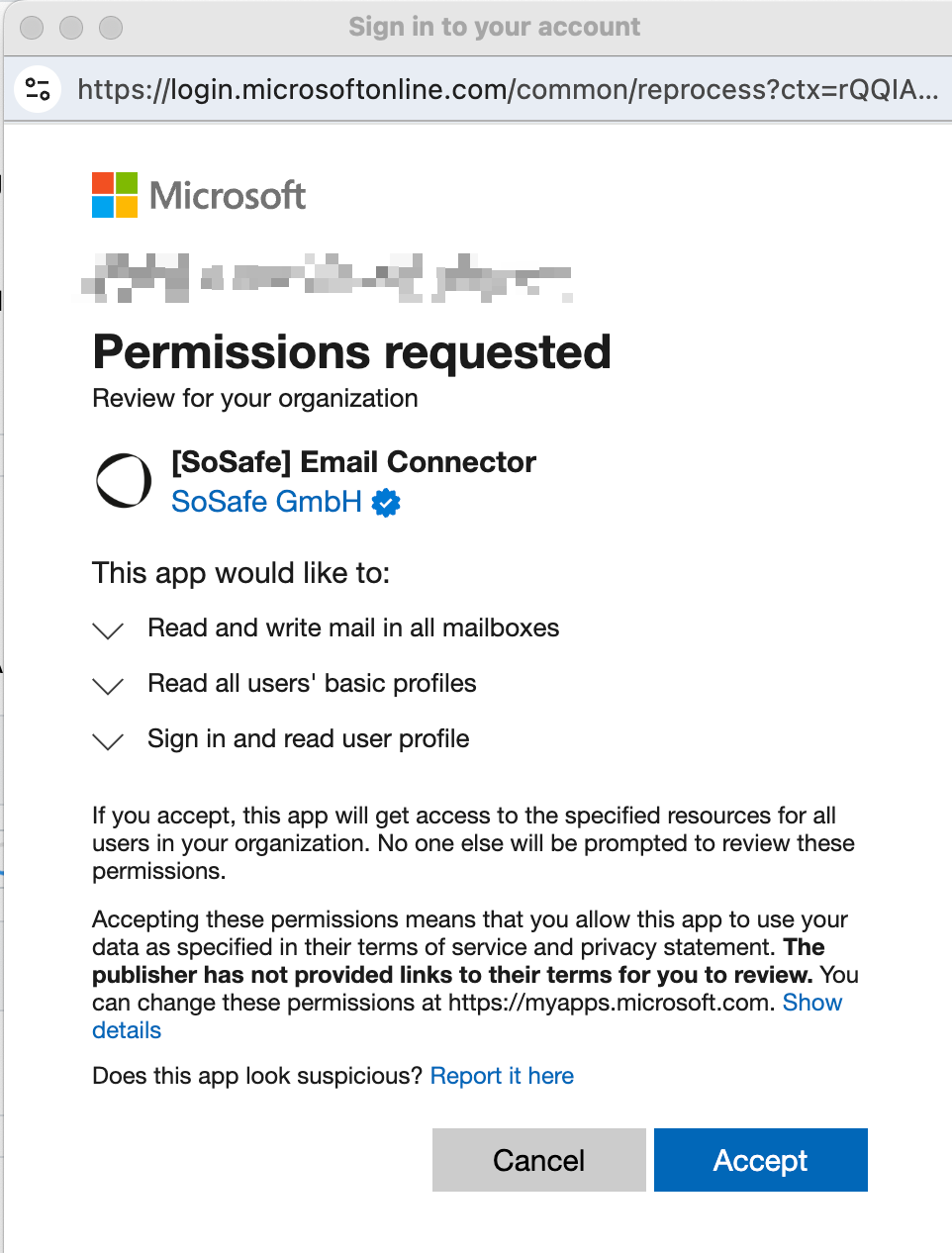
Click Accept on the Permissions requested page to authorize the integration.
If you do not have administrator rights:
Click I’m not an admin.
Ask the Microsoft Entra admin for the organization’s Tenant ID.
Enter the Tenant ID in the corresponding field and select Generate consent link.
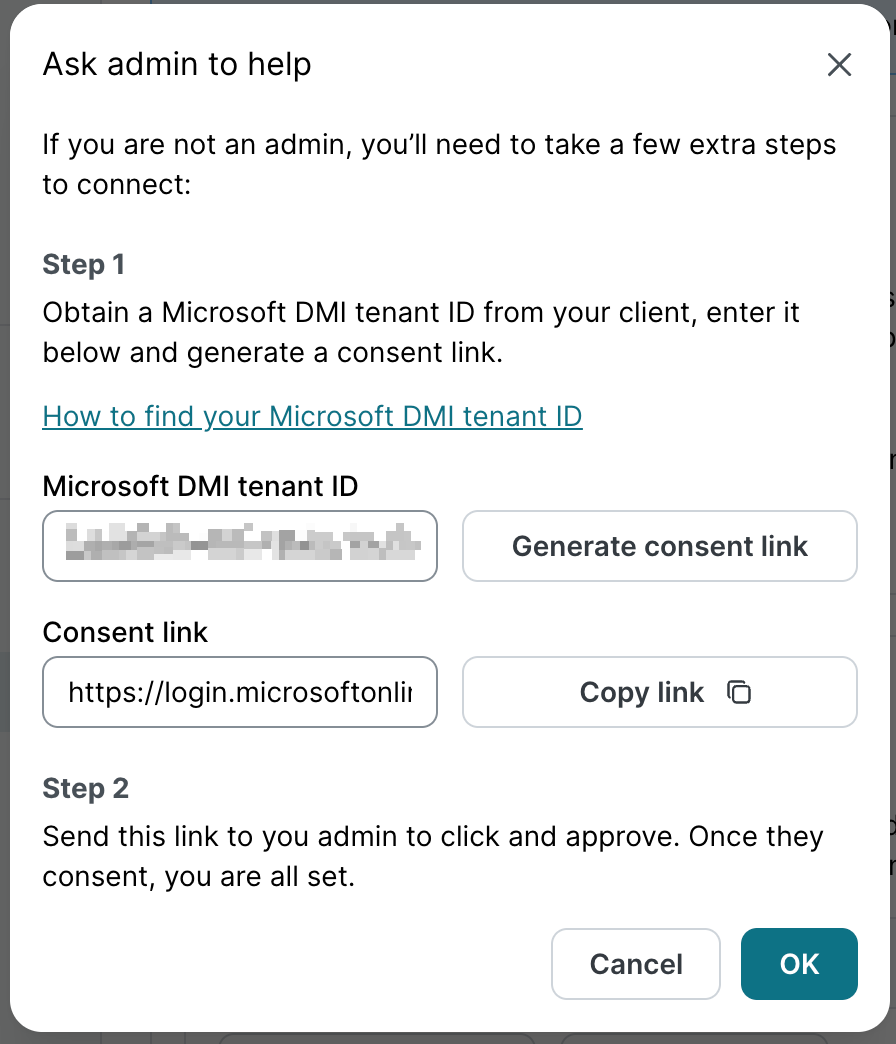
Select Copy Link and send this link to your Microsoft Entra admin to approve the authorization.
The Microsoft 365 DMI Whitelisting menu should now show the Waiting for confirmation status.
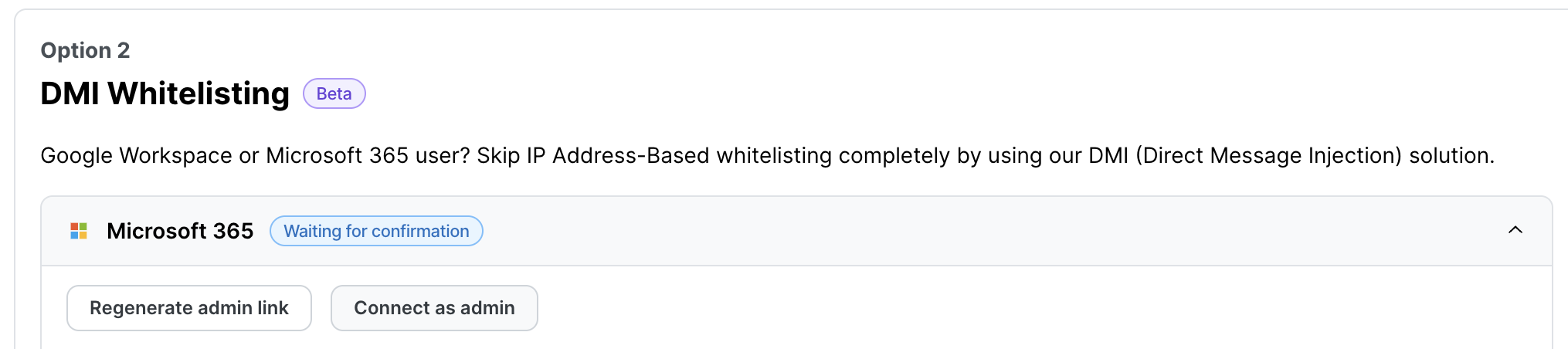
For the first scenario, or once the admin has approved the authorization, the Microsoft 365 DMI Whitelisting menu should now show the Connected status.
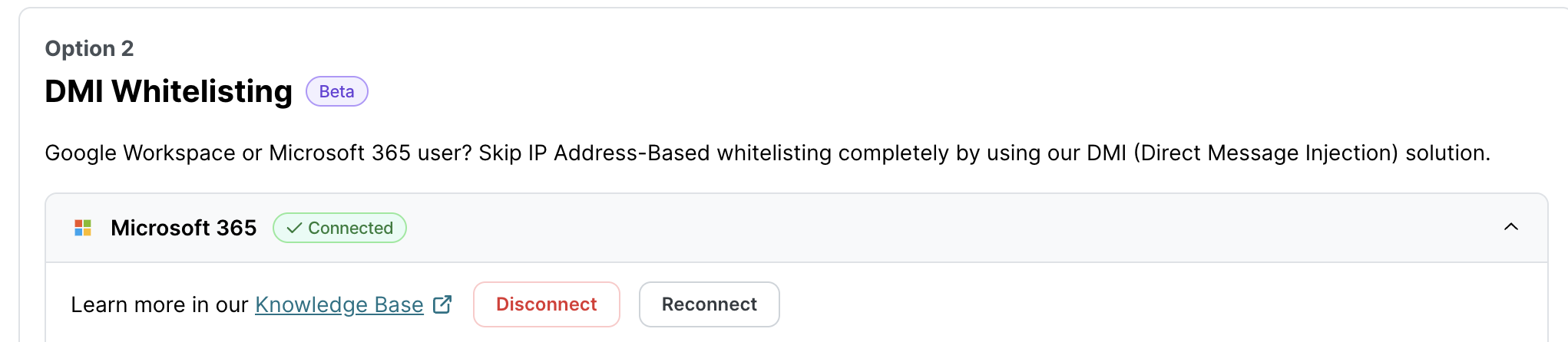
Important: Once the admin has approved the authorization, refresh the Whitelisting page to check the updated connection status.
Removing Microsoft 365 DMI integration
To entirely remove the Microsoft 365 Direct Message Injection (DMI) whitelisting setup, follow these two steps:
Disconnect the SoSafe DMI connector by clicking on Disconnect. This step is initiated and completed from within the SoSafe Partner Platform. Once disconnected, no further emails will be injected via DMI.
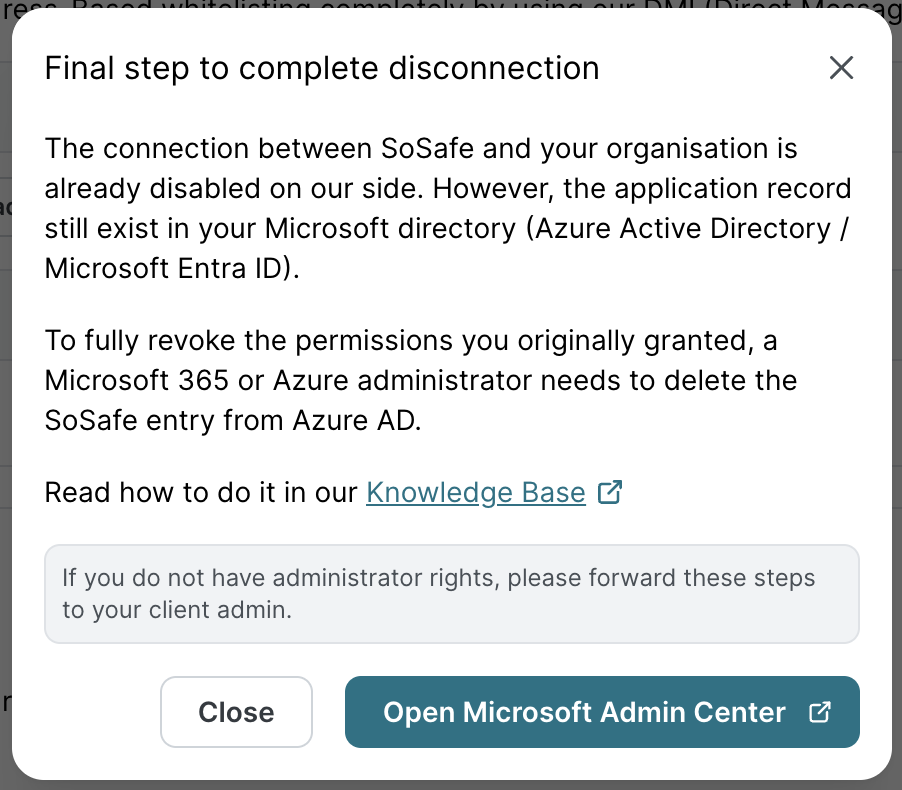
Then, to entirely revoke the SoSafe Email Connector permissions from the client side, a Microsoft Entra Admin must manually remove the SoSafe app from the Entra ID Enterprise apps list.
Open the Microsoft 365 Admin Center.
Open the Microsoft Entra admin center and click on Enterprise apps.
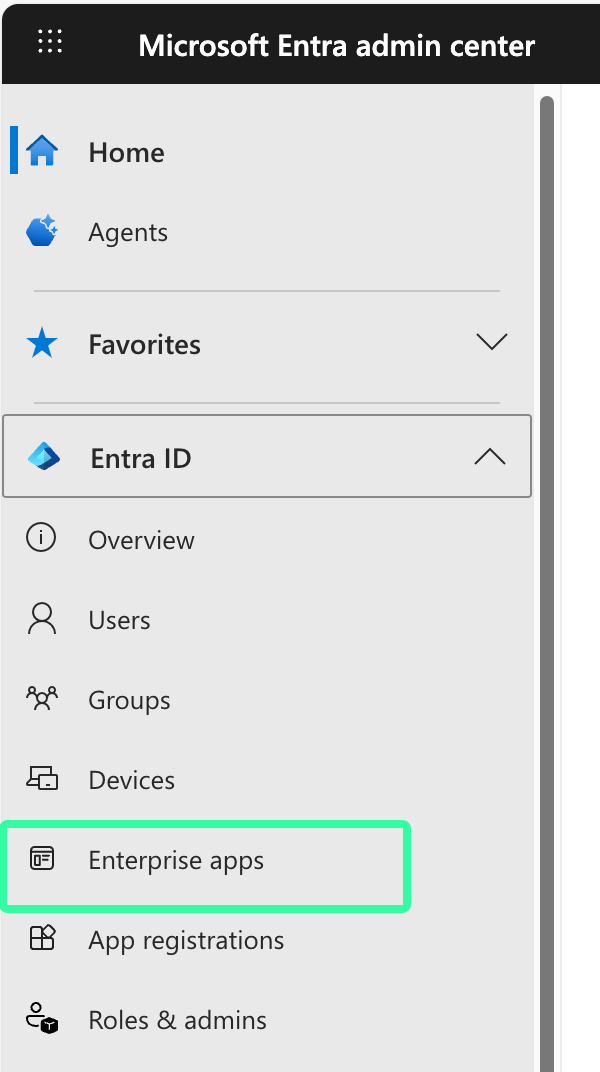
c. Under All applications, select [SoSafe] Email Connector.
d. In the Overview page, click on Properties and then click on Delete.
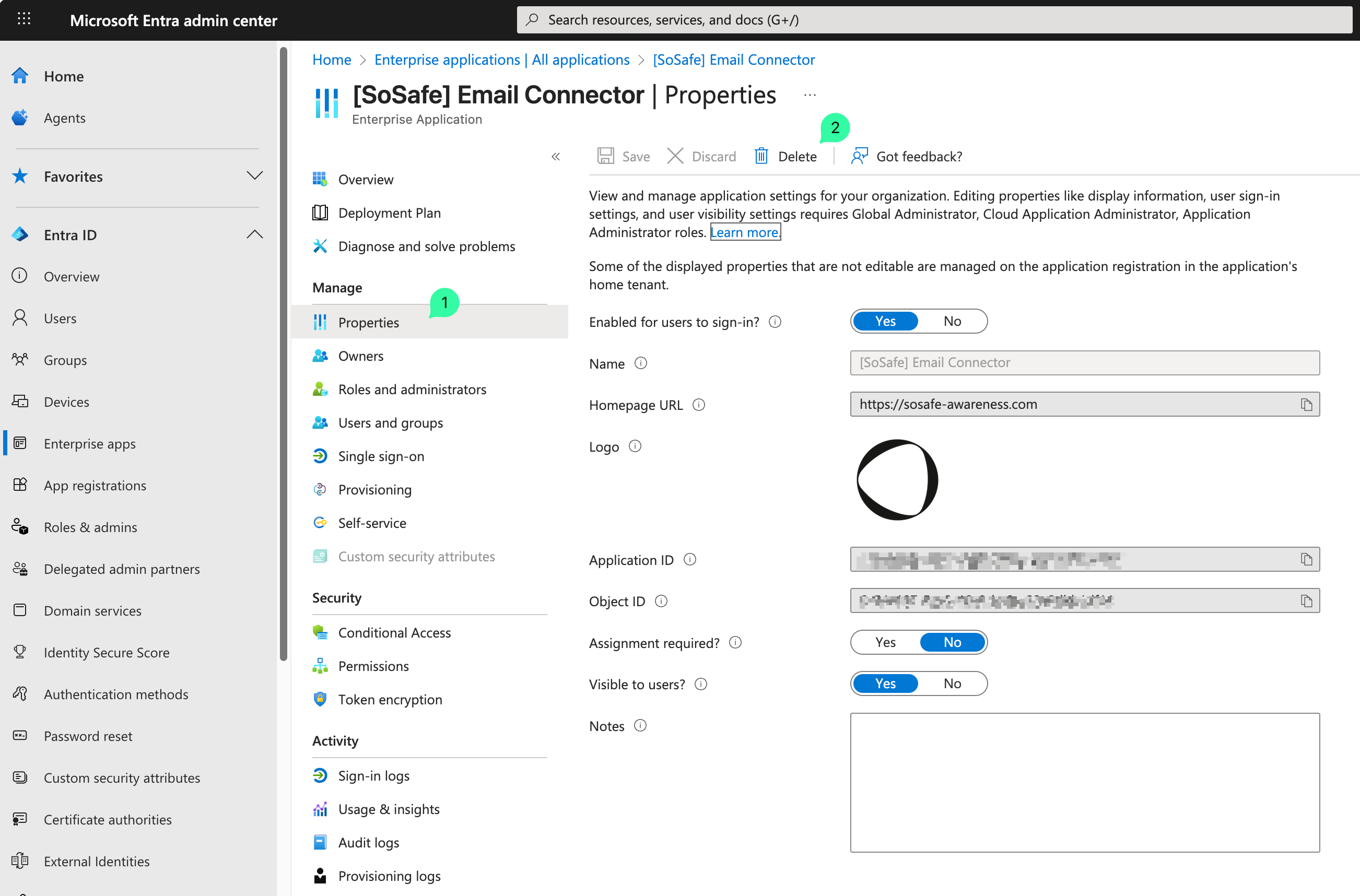
e. In the confirmation page, click Yes.
