(DEPRECATED) Whitelisting Guide - Partner Platform
Whitelisting Options
Client email whitelisting (allowing SoSafe senders and domain lists to bypass spam filters) is required to ensure the simulation emails reach your client employees' inboxes. In addition, this configuration will enable the client’s employees to access the learning pages they are supposed to see if they click on one of these simulated emails.
We suggest initiating this process early during client setup, as it requires a clear understanding of the current email security landscape and the necessary permissions for configuring these settings. Following these instructions ensures that our simulated phishing emails - and only those - can bypass your client’s email filters.
To allow partners to adapt to each client's technological stack and requirements, we offer two interchangeable whitelisting options: Header Token-Based and IP Address-Based.
Only configure one of the approaches at a time for each client. Setting both Header Token-Based and IP Address-Based whitelisting may lead to misconfiguration, making troubleshooting much harder.
Header Token-Based Whitelisting
Email Header Token-Based whitelisting is a security method that controls which emails can reach employees' inboxes. It works like a secret password in the email's header information.
An email consists of the header and the body. The header usually contains information like the sender's address, IP address, the time the mail was sent, etc. Most of this information is stored in the header's code and is only visible if we examine the header and its properties. Email headers can be provided with a digital token that authenticates the sender. The receiving mail server verifies the signature using a public key stored on the DNS server.
This method offers a one-time configuration, provided the digital token remains unchanged. Consequently, when new phishing simulation templates are introduced, the client's Header Token-Based Whitelisting settings need not be updated in the future.
How do I set up Header Token-Based Whitelisting?
Get the Customer Key and Value:
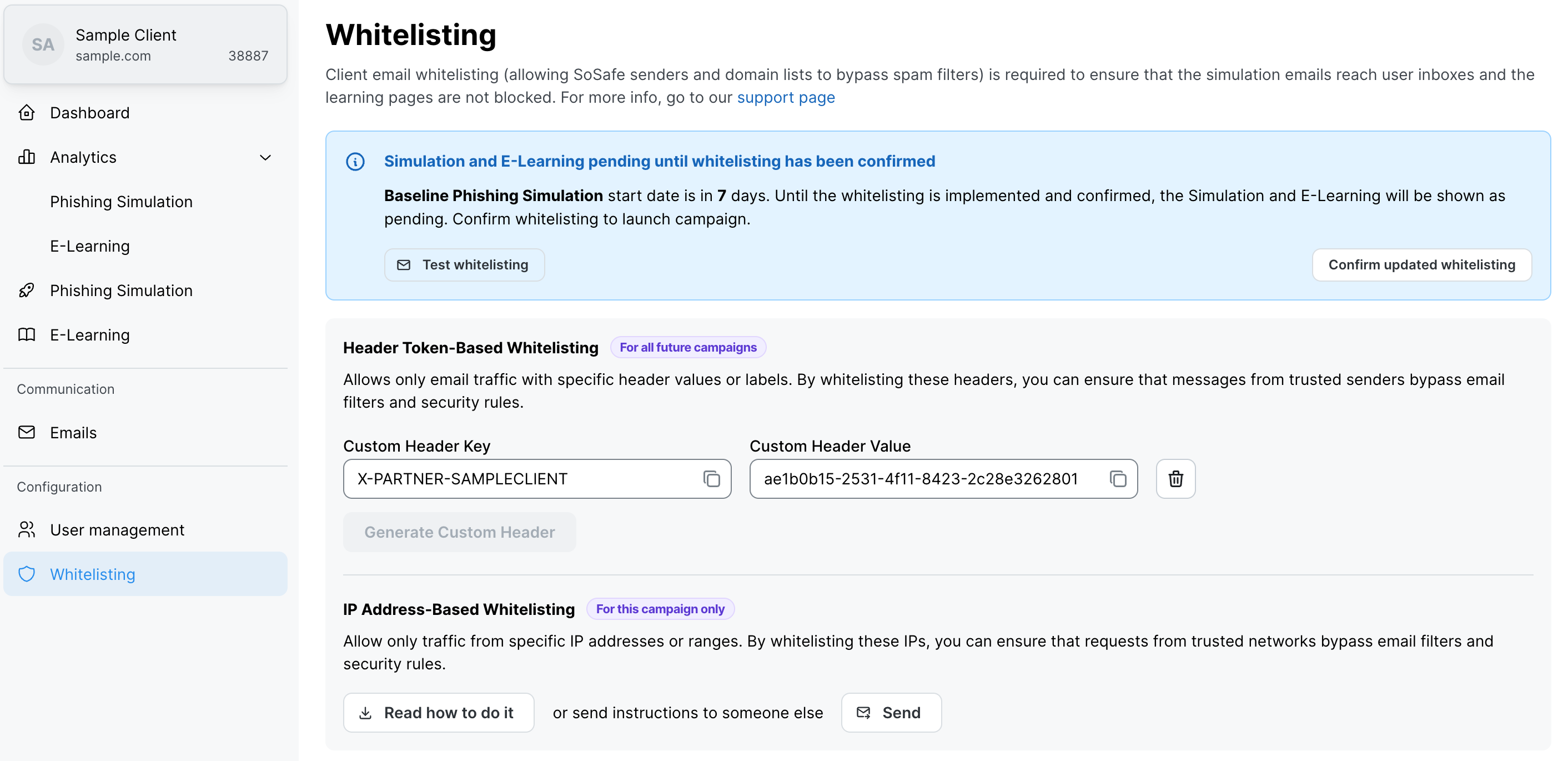
Go to the client settings in SoSafe’s Partner Platform and open the Whitelisting menu.
From there, you can copy this client’s unique Customer Header Key and Customer Header Value, as shown in the example below.
The Header Key and Value needs to be unique for your company. We recommend using a UUID Generator tool to create the Header Value.
Microsoft 365 Header Token-Based Whitelisting:
In Microsoft 365, two mail flow rules need to be configured.
Bypass Clutter and Spam Filtering
To bypass the Clutter and Spam Filtering please follow these steps:
Open the Office 365 Exchange admin center
Under Mail flow, open the Rules menu, click +Add a rule, and then select the option Create a new rule
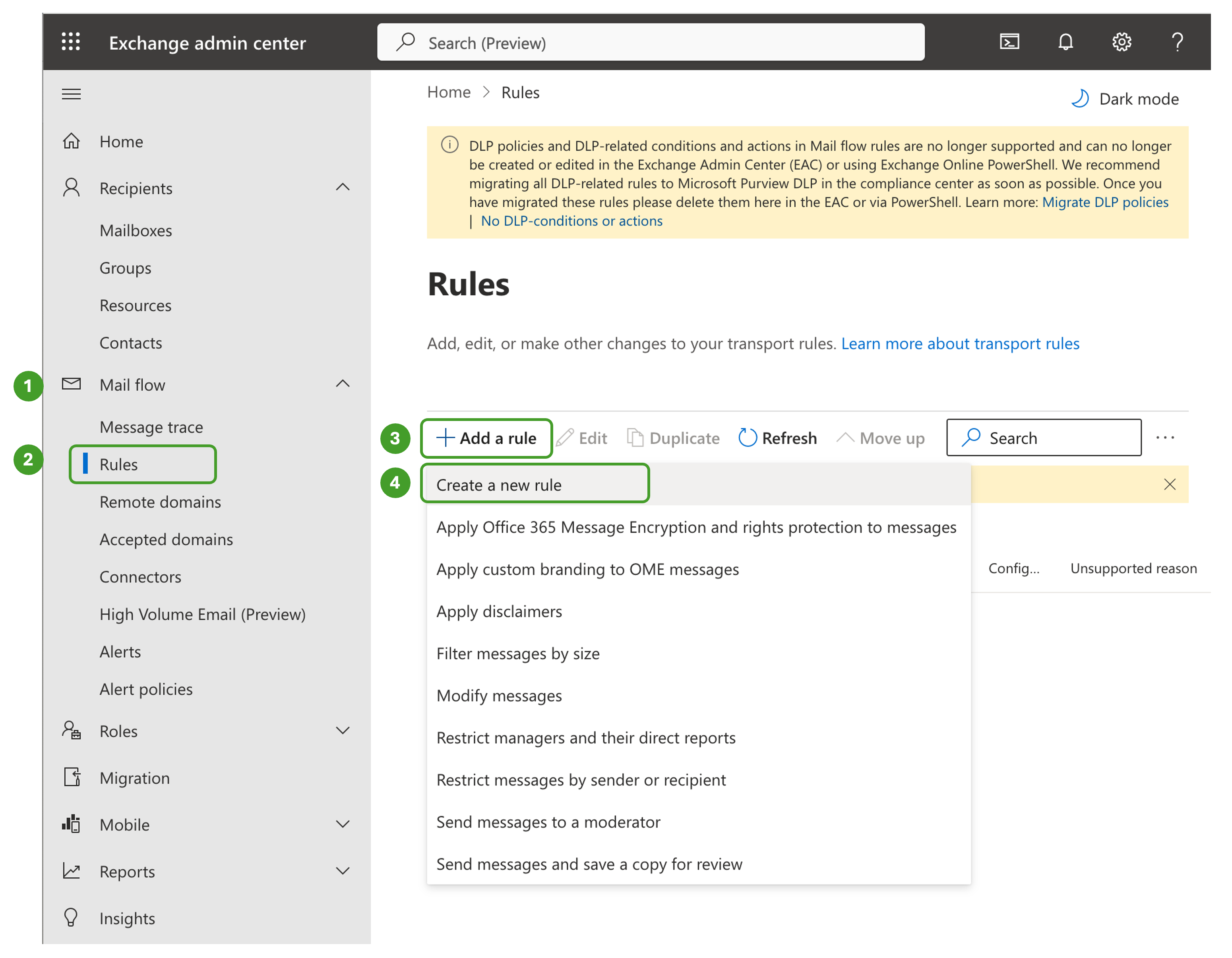
Under New transport rule:
Insert a descriptive name like “SoSafe Phish Simulation Bypass Clutter and Spam Filtering”
In Apply this rule if, select the options The message headers… and includes any of these words and then:
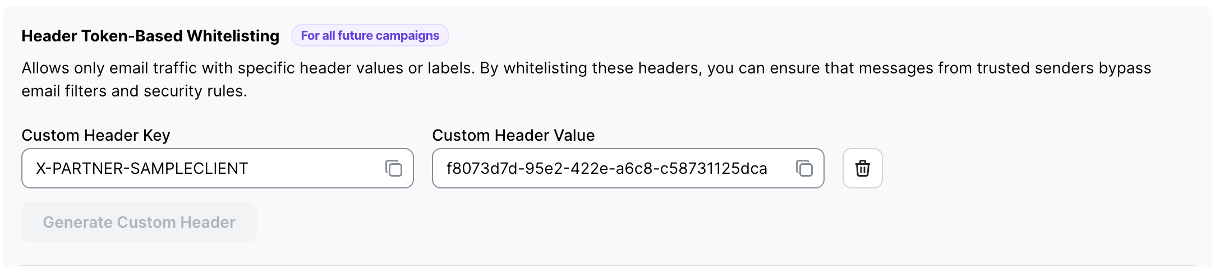
Enter the Custom Header Key from SoSafe’s Whitelisting Menu (“X-PARTNER-SAMPLECLIENT” in the above example) in specify header name
Enter the Customer Header Value from SoSafe’s Whitelisting Menu (“f8073d7d-95e2-422e-a6c8-c58731125dca“ in the above example) in specify words or phrases
In Do the following, select the option Modify the message properties and set the spam confidence level (SCL) to Bypass spam filtering
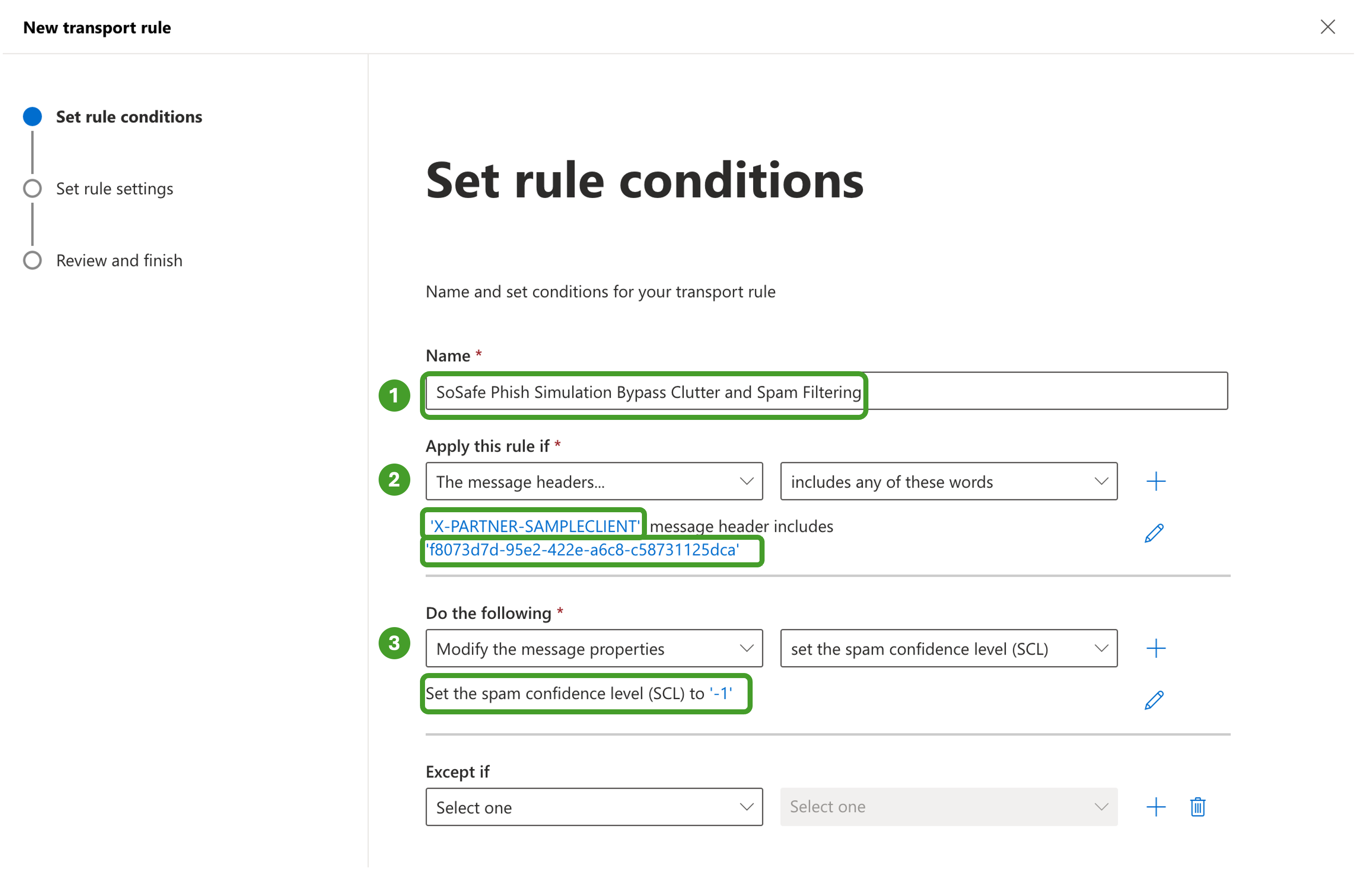
Then, in Do the following, click the + sign
i. Select the Modify the message properties and set a message header
ii. Enter “X-MS-Exchange-Organization-BypassClutter“ and set the value to “true”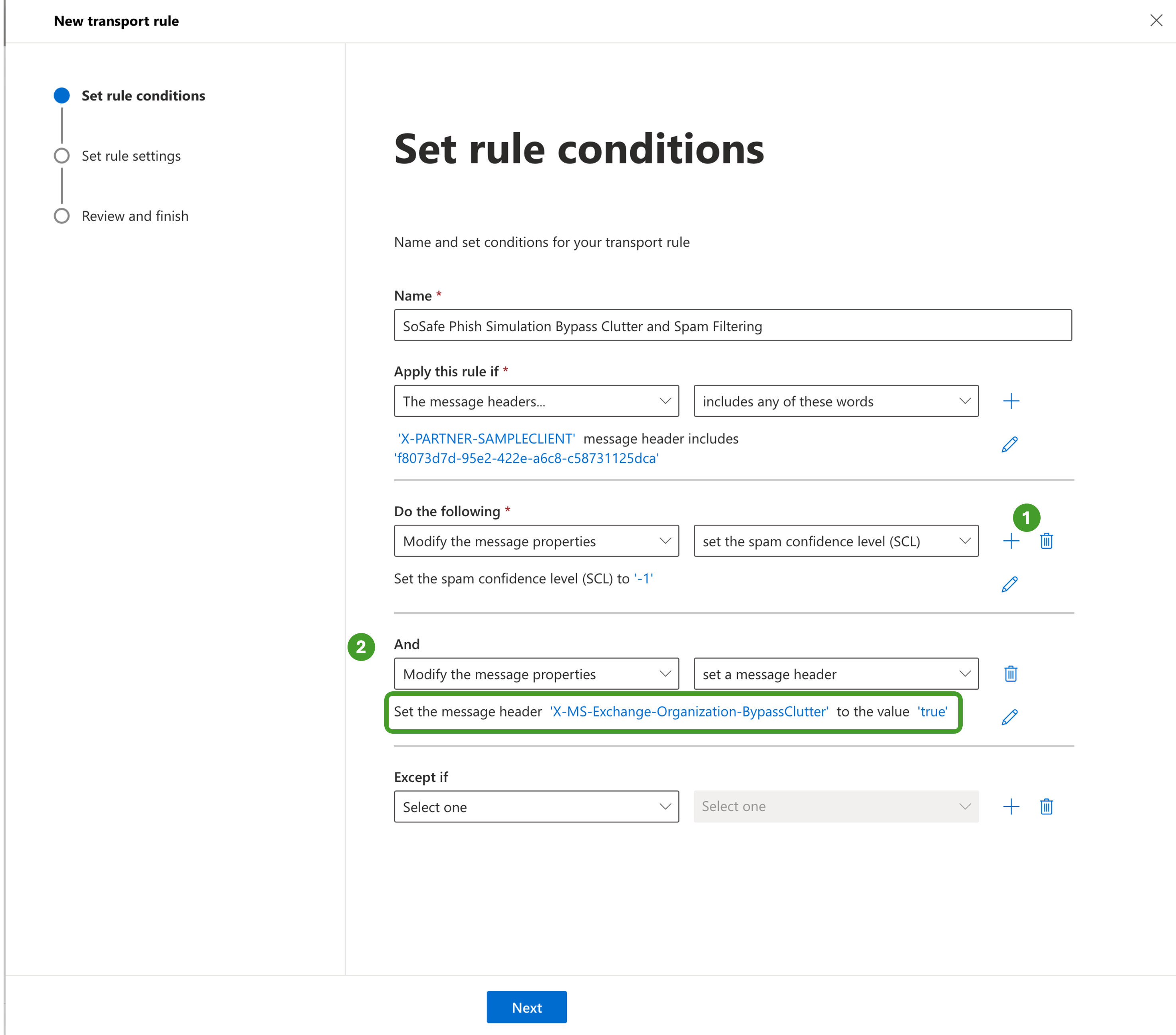
Click Next
Under Set rule settings, click Next
Under Review and finish, click Next
Bypass the Junk Folder
To bypass the Junk Folder use the same flow from Bypass Clutter and Spam Filtering with the following steps:
Open the Office 365 Exchange admin center
Under Mail flow, open the Rules menu, click +Add a rule, and then select the option Create a new rule (the same flow as above)
Under New transport rule:
Insert a descriptive name like “SoSafe Phish Simulation Bypass the Junk Folder”
In Apply this rule if, select the options The message headers… and includes any of these words and then:
Enter the Custom Header Key from SoSafe’s Whitelisting Menu (“X-PARTNER-SAMPLECLIENT” in the above example) in specify header name
Enter the Customer Header Value from SoSafe’s Whitelisting Menu (“f8073d7d-95e2-422e-a6c8-c58731125dca“ in the above example) in specify words or phrases
In Do the following, select the option Modify the message properties and set the spam confidence level (SCL) to Bypass spam filtering
Then, in Do the following, click the + sign
i. Select the Modify the message properties and set a message header
ii. Enter “X-Forefront-Antispam-Report“ and set the value to “SFV:SKI;”
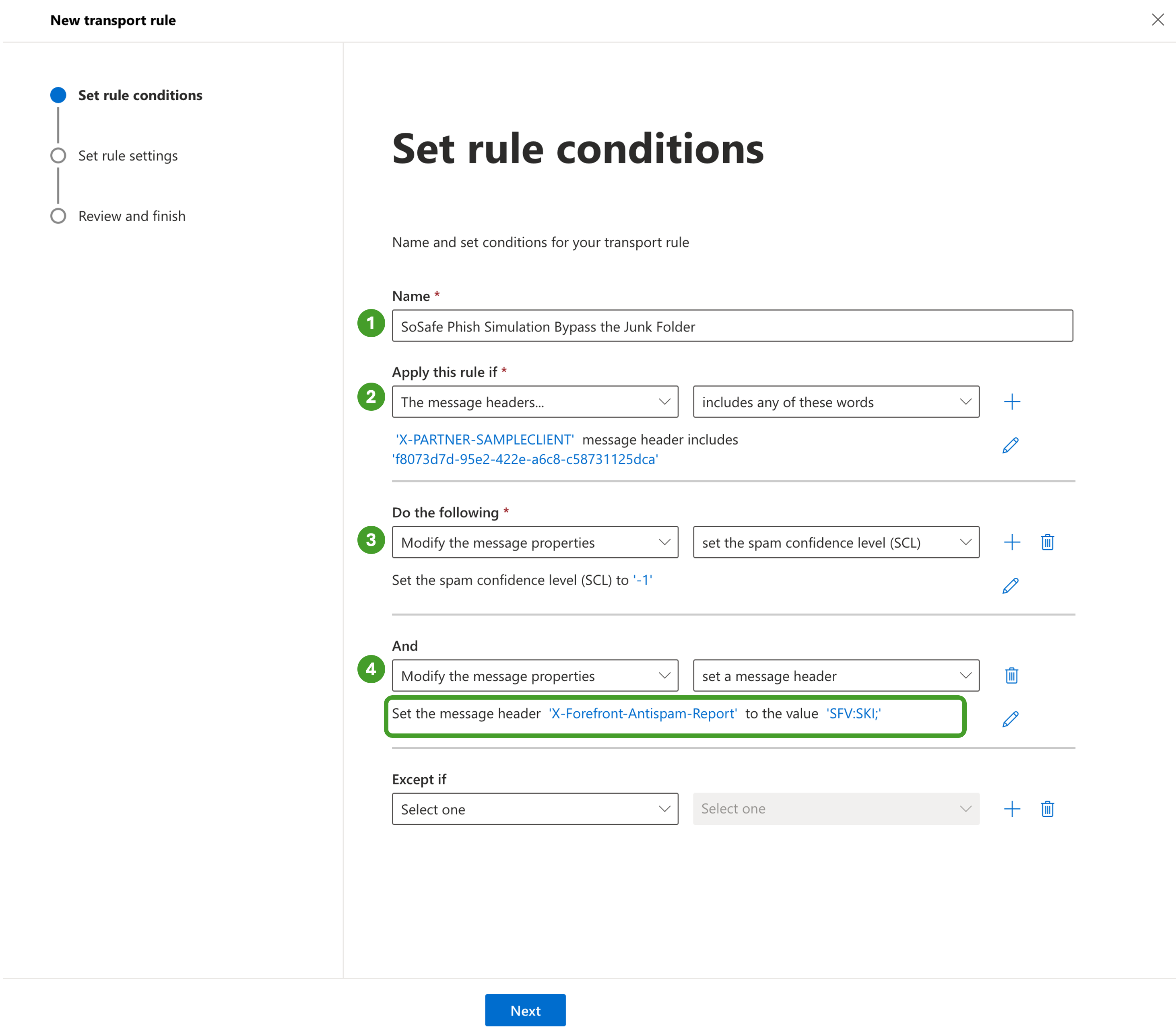
e. Click Next
Under Set rule settings, click Next
Under Review and finish, click Next
Activate Mail Flow rules
The new mail flow rules are disabled by default. To enable the rules:
Click on each rule name to open the details
Then click the Enabled toggle
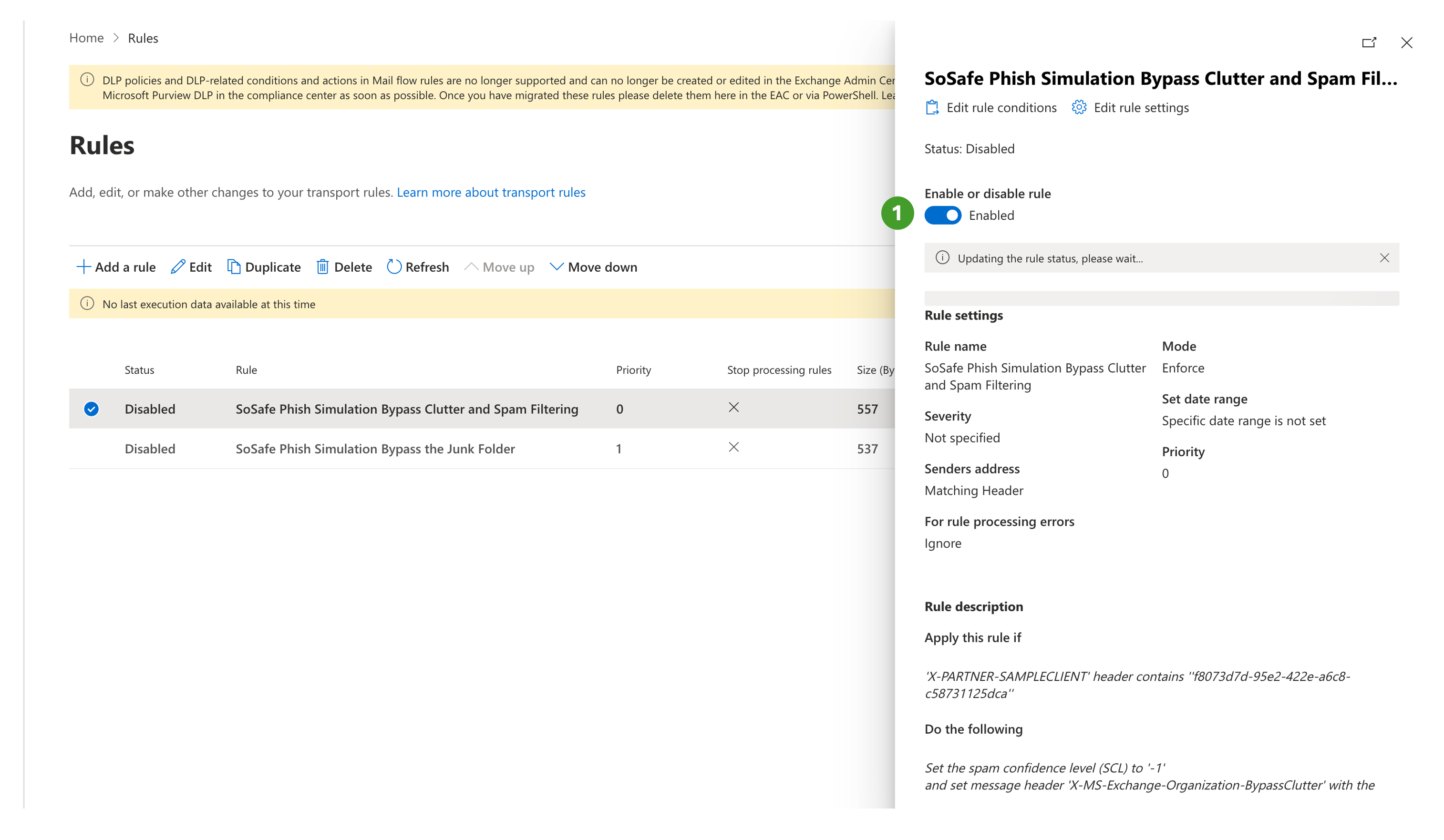
Repeat this process for the second rule and check that both rules' status is Enabled.
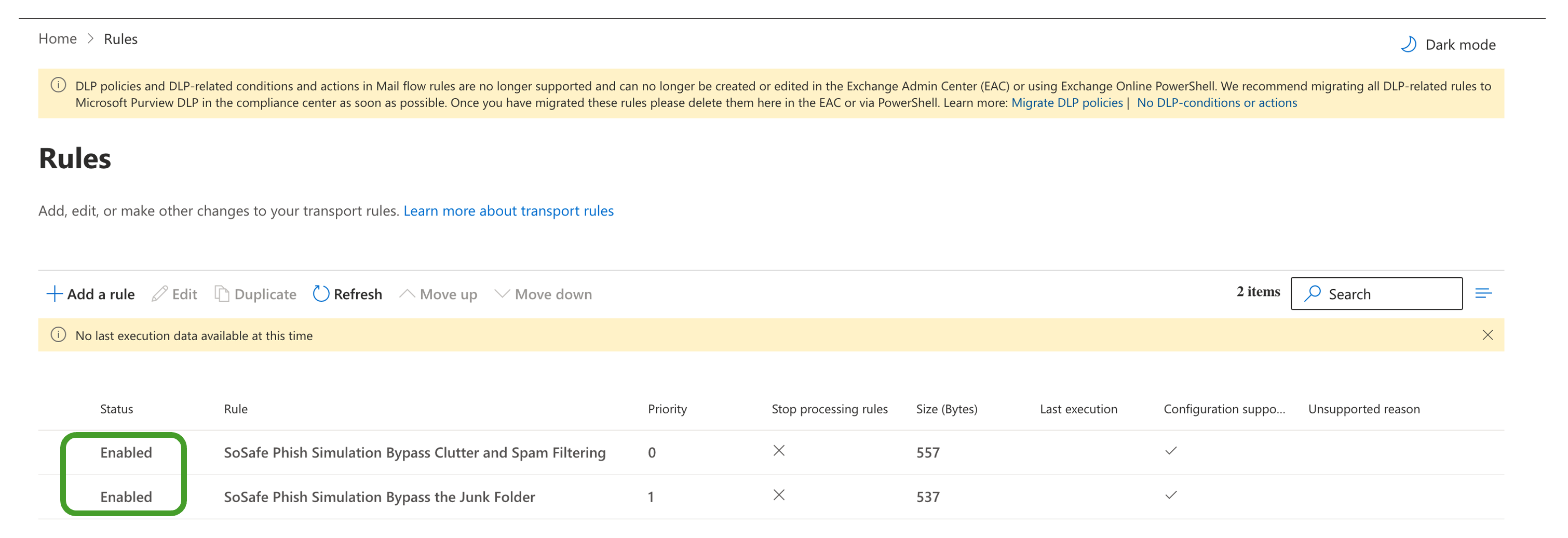
IP Address-Based Whitelisting
IP Address-Based Whitelisting is a security method that ensures training emails come only from authorized sending servers, helping to distinguish legitimate training from actual phishing attempts.
It contains a list of approved IP addresses for SoSafe’s Phishing Simulation platform to avoid conflicts with regular email security systems.
The release of new phishing simulation templates may introduce new envelope senders or URL domain entries. This means that IP Address-Based configurations will need to be updated to guarantee that the new simulation emails can bypass the email security filters.
How do I set up IP Address-Based Whitelisting?
1. Get the Customer Key and Value:
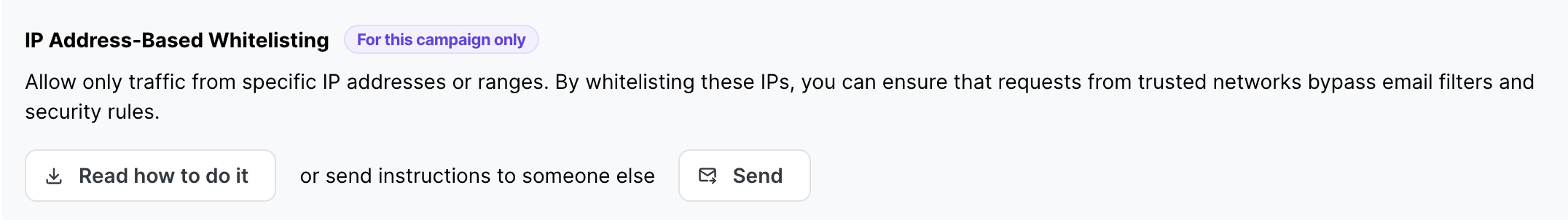
Go to the client settings in SoSafe’s Partner Platform and open the Whitelisting menu.
From there, you can download the whitelisting guide (“SoSafe Whitelisting Manual.pdf”) by clicking on the Read how to do it button or email it to someone else by clicking on the Send button.
2. Microsoft 365 IP Address-Based Whitelisting:
In Microsoft 365, to ensure that all simulated phishing emails reach their intended recipients, advanced delivery must be set up by following these steps:
Under Email & collaboration, select Policies & rules and then Threat policies
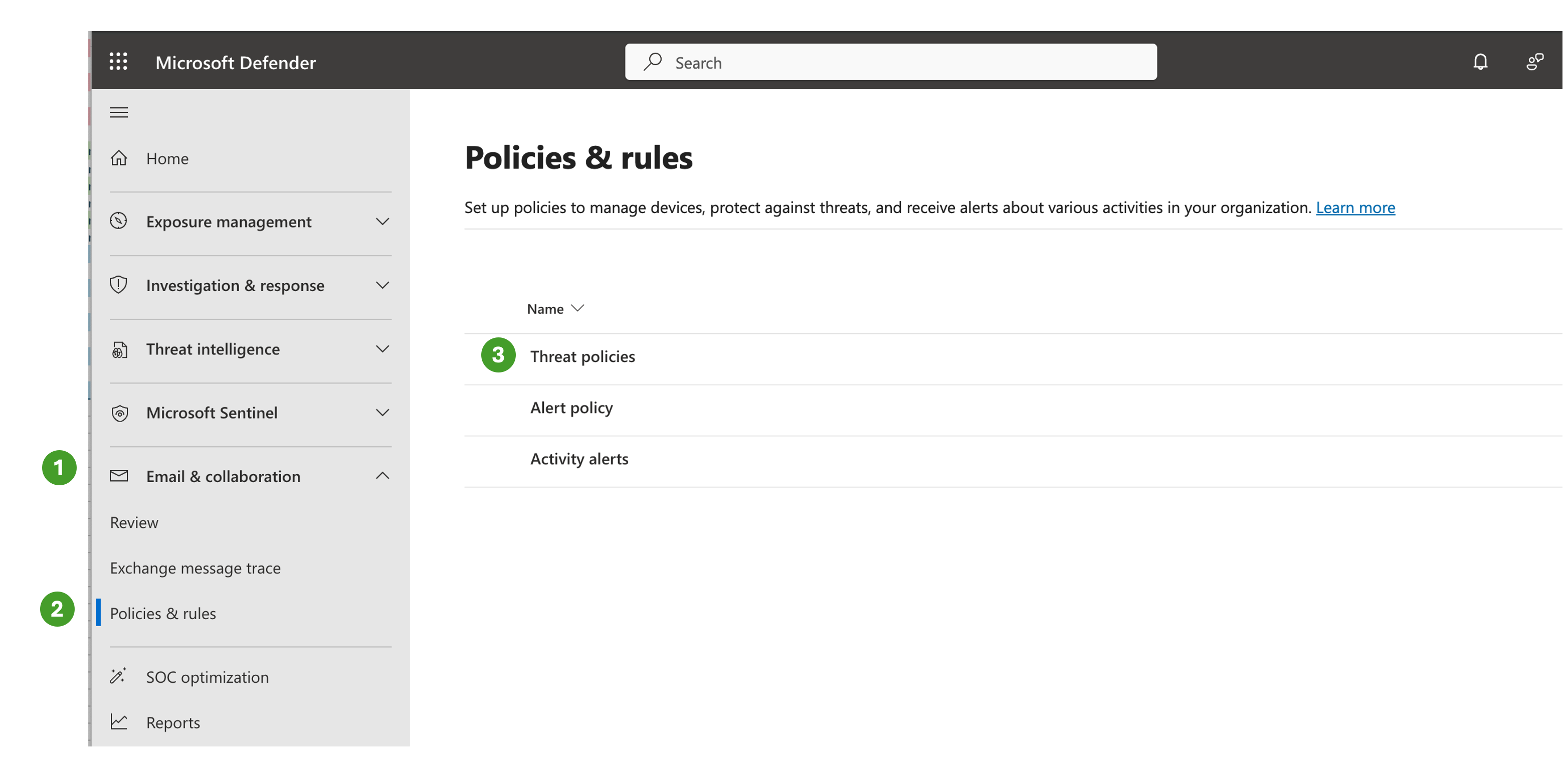
Under Threat policies, go to the Rules group and select Advanced delivery
Here, select the tab called Phishing simulation and then select Edit. A new window titled Edit third party phishing simulations will open
In the corresponding fields, enter the whitelisting information provided in the “SoSafe Whitelisting Manual.pdf”, as follows:
The domains provided under Envelope sender addresses (technical senders) belong in Sending Domain on the Microsoft page. Note that only the domain, the part after the @ (name@domain.com), should be added here, not the entire address.
The IPv4 addresses provided under SoSafe mail servers belongs in Sending IP on the Microsoft page.
The domains/URLs provided under List of used domains in the phishing links belong under Simulation URLs to allow on the Microsoft page. Please use the following format: "~example.com~".
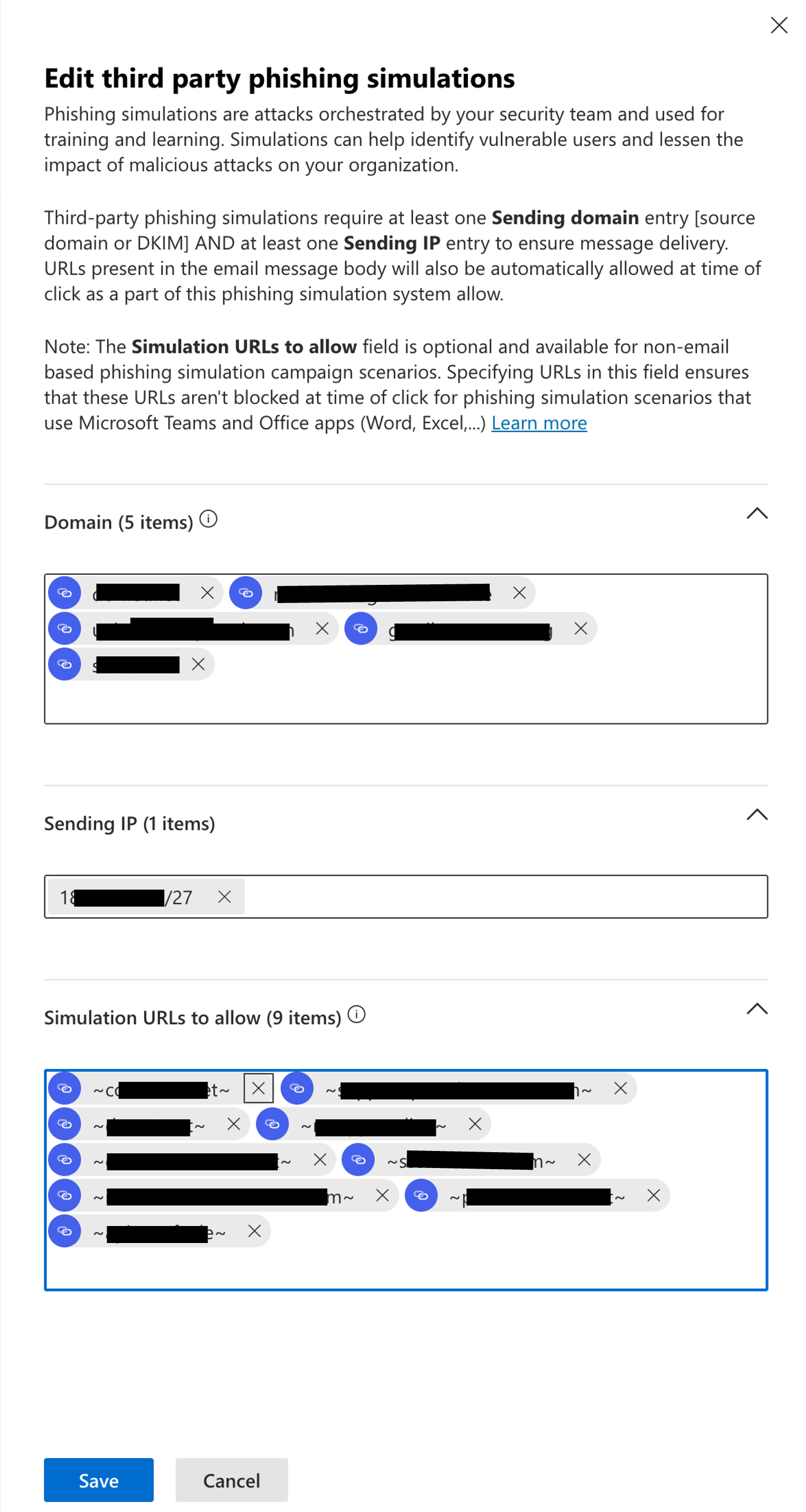
Select Save to finish the process. It may take some time for the changes to take effect.
Confirm Whitelisting configuration
Regardless of the whitelisting approach, because clients may have multi-layer security systems, it is paramount always to test that whitelisting is working as expected after the configuration.
To do so, send all test emails to an inbox that uses your client’s domain, then have the client check whether they were all received. In addition, the customer should check whether they are being forwarded to the micro-learning pages correctly when clicking the links.
Go to the client settings in SoSafe’s Partner Platform and open the Whitelisting menu
Click on the Test whitelisting button, and enter an email address belonging to the client’s email domain
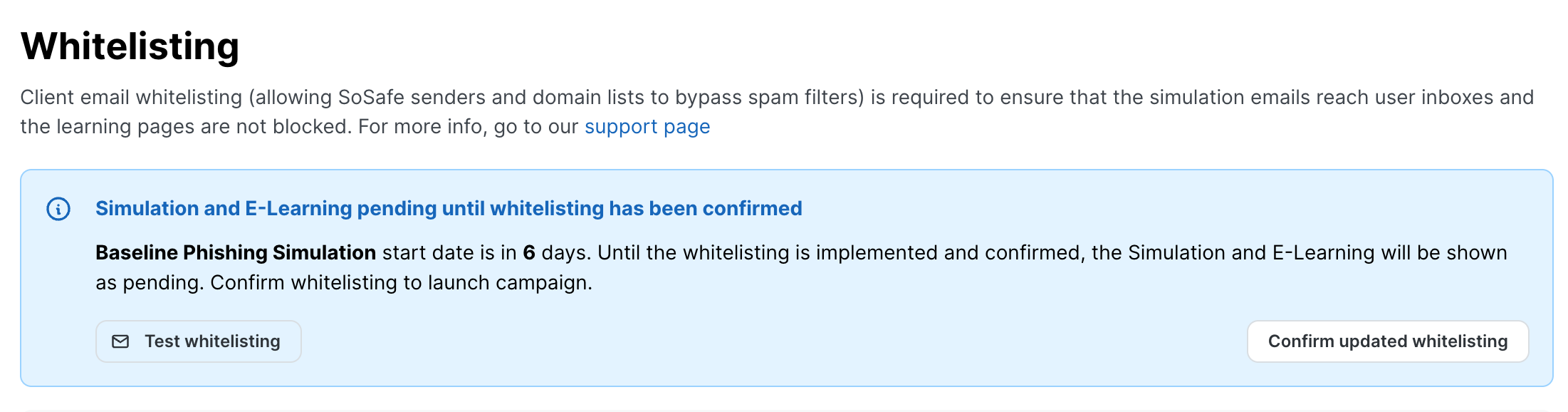
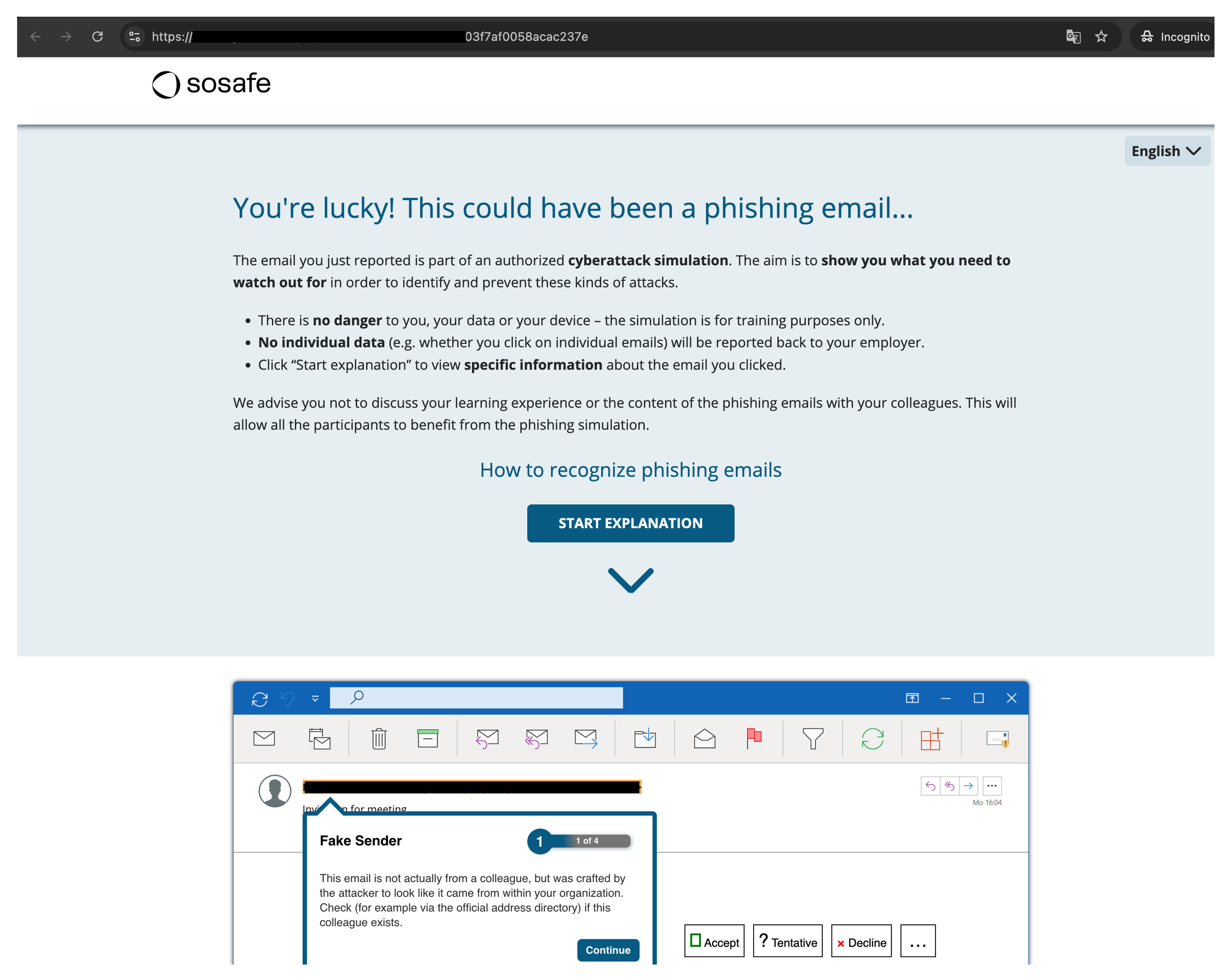
Open the client’s email to validate that the Phishing Simulation emails are in the inbox
Then click on the email body links to confirm access to the micro-learning pages (like the example from below)